Navigating Tomorrow's Tech Today
Top Headlines
How Privacy Tech Is Rebuilding the Internet’s Core Systems
Mojeek, Punkt, and iProVPN solve separate problems, but their value compounds through alignment. .
Apple Taps Google’s AI to Power Siri Overhaul in Unlikely Alliance
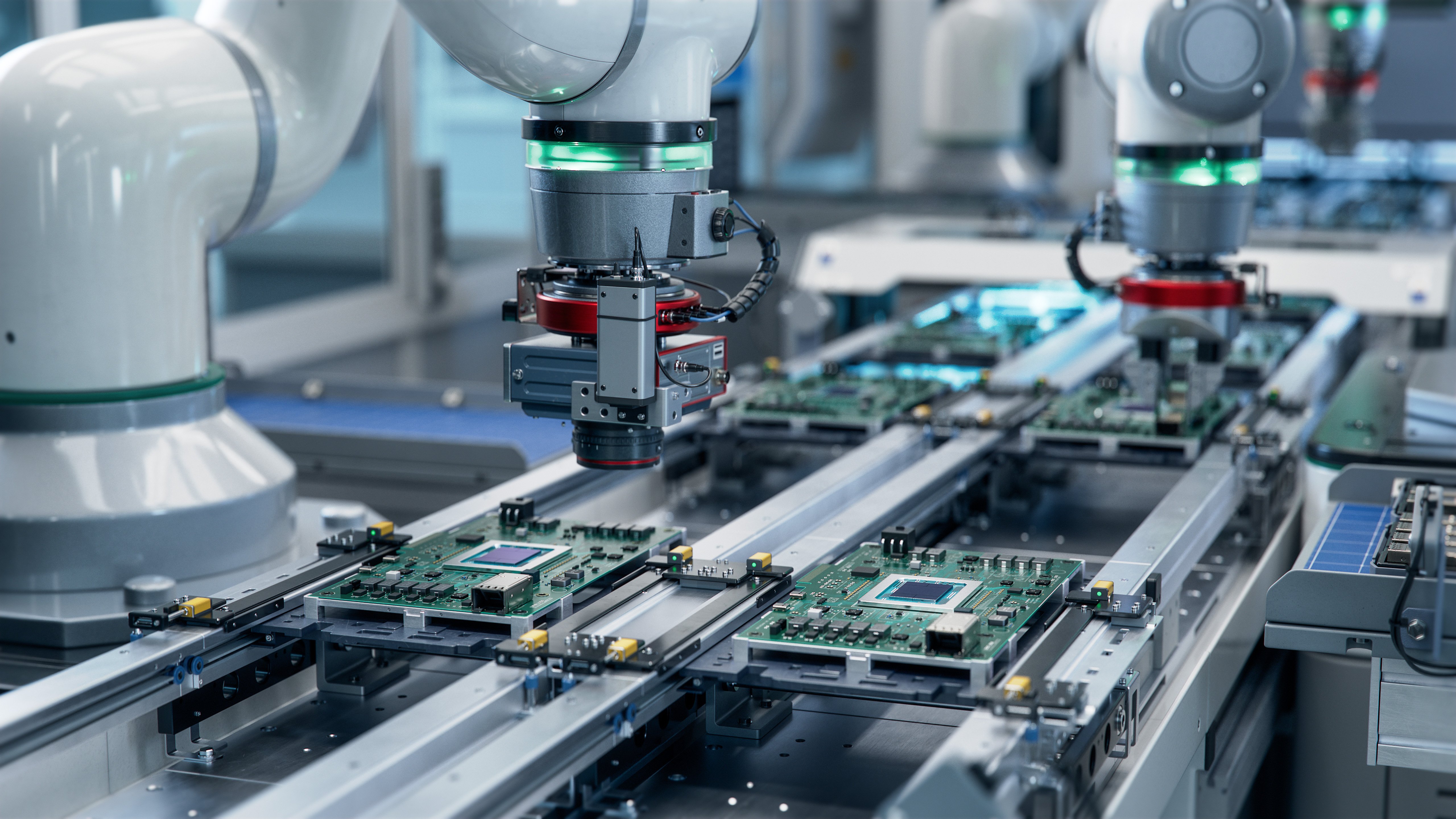
AI-powered DevOps Becomes Key to Speed and Scale
1
IBM Bets on Built-in Data Compliance to Meet Digital Sovereignty Needs
2
China’s Espionage Playbook Focuses on Congress’s Inner Layer
3
AI Hallucinations and M&A: Why Risk Management Must Catch Up
4
German Green Fintech Cloover Secures $1.22 Billion in Home Clean Energy Bid
5
The ChatGPT Incident That Put Trump’s Cyber Chief Under Scrutiny

In Case You Missed It: Steps to Closing the Cybersecurity Gender Gap, Apple Partners with Google to Bring Gemini to Siri, a Closer Look at Salt Typhoon’s Methods
As we celebrate International Women's Day, Tech-Channels explores ways to closer the gender gap and Apple pairs with Google to bring Gemini...

In Case You Missed It: Arkose Labs CEO Discusses Managing AI Agents, UK Okays Cross-border Card Fees, CISA Interim Chief Under Scrutiny After Feeding Sensitive Documents into Public ChatGPT
Arkose Labs CEO lays out how to manage AI agents while CISA interim chief learns a lesson about using public ChatGPT and Cloover secures $1...

In Case You Missed It: Presidential Approaches to Cybersecurity, Google's Wiz Acquisition Europe on Edge, U.S. War Plans for AI
Presidents' cyber policies often outlive their administrations and give their successors something to build upon while credit rate cap spur...

In Case You Missed It: Romance Scams, Vindictive Exes Up Enterprise Risk, Cyber Experts Profess Love for Tech, M&A Soars in Banking and AWS Makes a Play for Sovereign Cloud
Defenders need to pay more attention to the enterprise risk posed breakups and romance scams while banks are pursuing M&As with gusto.

In Case You Missed It: DevSecOps Feels the Effects of AI, Preparing for Ransomware Aimed at ERP, Look Behind the Scenes of a Super Bowl
Boards need to pay more attention to the risks posed by ERP systems and AI will accelerate DevOps and Hydrolix shows what it's like to run ...

In Case You Missed It: Sovereign Cloud Surges in Europe, AI Agents Do Really Well in CTF Competitions, EU Dilutes Sustainability Reporting Rules
This week reporting centered around sovereign cloud, Ai agents' stellar performance in CTF competitions and Fidelity's upcoming stablecoin.

84% of Banks Have Completed an M&A Deal With an Eye on Modernization
Community and regional banks increasingly are viewing M&A as a springboard for modernization.
70% of Banks Report Technology Infrastructure Spend to Increase in 2025
Modernization is a must to remain competitive and requires a strong blend of investment in technology and human-centric banking.

Europe Sees Surge in Sovereign Cloud Solutions at the Expense of US Hyperscalers
Europe is fast pivoting towards sovereign cloud solutions that offer data residency and jurisdictional control away from the oversight of U...
The Role of AI in Email Security and How Real-Time Threat Intelligence Can Supercharge Your SOC Team
| Virtual Event | Apr 18, 2024 | 5:30PM - 6:45 PM ET |
As email security measures have evolved, cybercriminals have adapted by employing more advanced attack methods, particularly artificial intelligence (AI), to circumvent existing protections. However, security defenders are harnessing the power of AI in innovative ways to strengthen their networks.
Hosted by KnowBe4 and Energize Marketing, this event brings together industry experts James McQuiggan, Security Awareness Advocate for KnowBe4, and Brandon Smith, Product Manager at KnowBe4, alongside our esteemed host David Steifman, TechEvents host and Managing Partner at Energize Marketing. Together, they will delve into the insights gleaned from KnowBe4's latest Osterman joint report on The Role of AI in Email Security, offering invaluable tips on harnessing AI to bolster your anti-phishing defense.
Don't let cybercriminals dictate the narrative. Empower your SOC team with the knowledge and tools they need to thwart emerging threats.
Learn More
Speakers
%20(4).png?width=126&height=126&name=James%20McQuiggan%20KnowBe4%20(200%20%C3%97%20200%20px)%20(4).png)
James McQuiggan
Security Awareness Advocate, KnowBe4

Brandon Smith
Product Manager at KnowBe4
%20(3).png?width=126&height=126&name=David%20Steifman%20(200%20%C3%97%20200%20px)%20(3).png)
David Steifman
Host TechEvents & Managing Partner, Energize Marketing

Megan Lynch
Lead Mixologist

Closing the Cybersecurity Gender Gap: 11 Steps That Matter
Cybersecurity’s future depends on the talent it cultivates today—and ensuring women have the opportunity to lead and thrive will be a criti...

Google Cloud: Five Strategic Threat Shifts for Cybersecurity in 2026
Here's what's likely to be on deck for cybersecurity in the coming year, according to Google Cloud’s newly released Cybersecurity Forecast ...

Top 5 GenAI Shifts That Tech Leaders Can't Afford to Miss in 2026
Rather than surveying the full horizon, we’ve selected five trends most relevant to enterprise strategy, operational resilience, and data-d...

Q&A: Arkose Labs CEO Lays Out Steps for Managing AI Agents
As it becomes clear that traditional security measure don't work, organizations must act now to develop a strategy for managing AI agents.

Q&A: Game On: Hydrolix Field CTO Karen Johnson Offers Behind-the-Scene Look at Running a Super Bowl
Gain expert insights into how Hydrolix commanded the Super Bowl behind the scenes to help Fox create a stellar viewing experience.

Q&A: Hydrolix CISO Josh Scott: There Is No 'S' in MCP, But There Should Be
Security leaders don't have visibility into MCPs, which AI users leverage to interact with systems in their ecosystems, says Hydrolix CISO ...
.png?width=1816&height=566&name=brandmark-design%20(83).png)
.png?width=204&height=52&name=brandmark-design-1024x0%20(3).png)
.png?width=180&height=50&name=brandmark-design-1024x0%20(4).png)









